################################################################################
모든 파일에서 문자열 검색
################################################################################
@@ R옵션 : 재귀검색
grep -R ‘New MySQL’ ./
추가 팁들
——————————————————————————–
Task: Display only words
——————————————————————————–
You can select only those lines containing matches that form whole words using the -w option. In this example, search for word ‘getMyData()’ only in ~/projects/ dirctory:
$ grep -w -R ‘getMyData()’ ~/projects/
——————————————————————————–
Task: Search for two or more words
——————————————————————————–
Use the egrep command as follows:
$ egrep -w -R ‘word1|word2’ ~/projects/
################################################################################
screen을 이용하여 터미널 화면 공유하기
################################################################################
@@ 먼저 ssh 또는 telnet 을 이용하여 서버에 접속한다음 screen 세션을 생성한다.
$ screen -S [세션명]
@@ 그리고 공동작업할 사람역시 해당 서버에 접속한다음 같은 세션명으로 다음과 같이 참여한다
$ screen -x [세션명]
@@ 이제 두 사람은 같은 화면을 보면서 동시 작업이 가능. 종료 : ctl-A D
################################################################################
awk와 cut 활용 : 인코딩 알아내기
################################################################################
@@ 자바파일들을 검색해서 Encoding이 iso-8859-1로 되어있는 것들을 찾아 UTF-8로 포맷을 바꿔준다.
——————————————————————————–
@@ ISO-8859-1 to UTF-8
——————————————————————————–
files=$(find ./ -name “*.java*” -type f);
for file in $files; do
encoding=`file -i $file | awk -F” ” ‘{ print $3 }’ | cut -c9-20`;
if [ ‘iso-8859-1’ = $encoding ]; then
iconv -f EUC-KR -t UTF-8 ${file} > ${file}.tmp && mv -f ${file}.tmp ${file};
else
echo “${file} was break”;
fi;
done;
################################################################################
SSHFS로 패스워드 없이 한큐로 마운트
################################################################################
echo “060606” | sshfs -p 5522 mbst@192.168.0.150:/home/mbst ~/SERVER -o uid=1001,gid=1002,password_stdin
echo “060606” | sshfs -p 5522 mbst@192.168.0.150:/home/mbst ~/Desktop/SAN/ -o uid=1001,gid=1002,password_stdin
@@ 먼저 ssh로 접속하여 한번 정도 로그인을 하는 것이 우선이다.
################################################################################
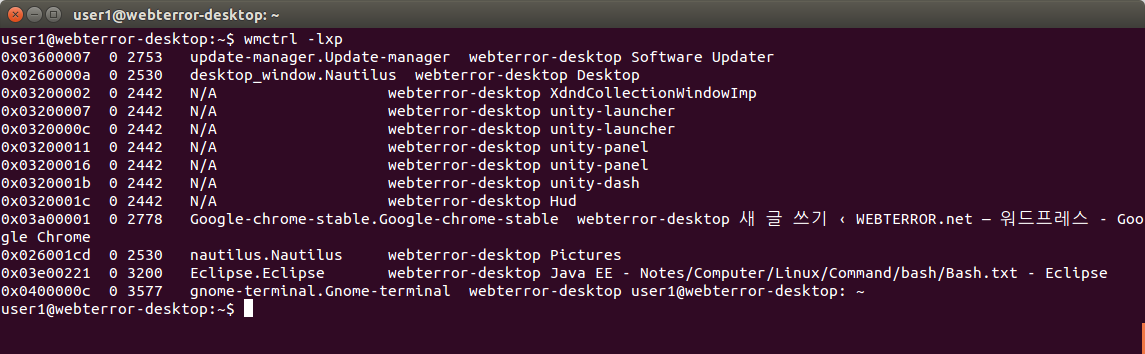
Gnome 윈도우 창별 프로세스 알아내기
################################################################################
sudo apt-get install wmctrl
wmctrl -lxp
그리고 필요한 윈도우 프로세스 번호를 알아내서 kill 시키면 될것이다.
################################################################################
파일 인코딩 바꾸기
################################################################################
iconv -f euc-kr -t utf-8 -o 서버사양.txt 서버사양.txt
@@ iconv 커맨드를 사용할 때 파이프로 파일에 쓰기기록을 하면 안된다. 동일한 파일을 읽고 동일한 파일에 쓰기를 하면 결과적으로 파일내용은 아무것도 없게 된다. 따라서 “-o” 옵션을 사용해서 파일에 재기록한다.
################################################################################
패킷 검사
################################################################################
——————————————————————————–
Display Captured Packets in ASCII using tcpdump -A
——————————————————————————–
$ tcpdump -A -i eth0
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 96 bytes
14:34:50.913995 IP valh4.lell.net.ssh > yy.domain.innetbcp.net.11006: P 1457239478:1457239594(116) ack 1561461262 win 63652
E…..@.@..]..i…9…*.V…]…P….h….E…>{..U=…g.
……G..7\+KA….A…L.
14:34:51.423640 IP valh4.lell.net.ssh > yy.domain.innetbcp.net.11006: P 116:232(116) ack 1 win 63652
E…..@.@..\..i…9…*.V..*]…P….h….7……X..!….Im.S.g.u:*..O&….^#Ba…
E..(R.@.|…..9…i.*…]…V..*P..OWp……..
——————————————————————————–
Display Captured Packets in HEX and ASCII using tcpdump -XX
——————————————————————————–
$tcpdump -XX -i eth0
18:52:54.859697 IP zz.domain.innetbcp.net.63897 > valh4.lell.net.ssh: . ack 232 win 16511
0x0000: 0050 569c 35a3 0019 bb1c 0c00 0800 4500 .PV.5………E.
0x0010: 0028 042a 4000 7906 c89c 10b5 aaf6 0f9a .(.*@.y………
0x0020: 69c4 f999 0016 57db 6e08 c712 ea2e 5010 i…..W.n…..P.
0x0030: 407f c976 0000 0000 0000 0000 @..v……..
18:52:54.877713 IP 10.0.0.0 > all-systems.mcast.net: igmp query v3 [max resp time 1s]
0x0000: 0050 569c 35a3 0000 0000 0000 0800 4600 .PV.5………F.
0x0010: 0024 0000 0000 0102 3ad3 0a00 0000 e000 .$……:…….
0x0020: 0001 9404 0000 1101 ebfe 0000 0000 0300 …………….
0x0030: 0000 0000 0000 0000 0000 0000 …………
——————————————————————————–
Capture the packets and write into a file using tcpdump -w
——————————————————————————–
$ tcpdump -w 08232010.pcap -i eth0
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 96 bytes
32 packets captured
32 packets received by filter
0 packets dropped by kernel
——————————————————————————–
Read packets longer than N bytes
——————————————————————————–
tcpdump -w g_1024.pcap greater 1024
——————————————————————————–
Read packets lesser than N bytes
——————————————————————————–
$ tcpdump -w l_1024.pcap less 1024
——————————————————————————–
Receive only the packets of a specific protocol type
——————————————————————————–
$ tcpdump -i eth0 arp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 96 bytes
19:41:52.809642 arp who-has valh5.lell.net tell valh9.lell.net
19:41:52.863689 arp who-has 11.154.12.1 tell valh6.lell.net
19:41:53.024769 arp who-has 11.154.12.1 tell valh7.lell.net
——————————————————————————–
Capture packets for particular destination IP and Port
——————————————————————————–
$ tcpdump -w xpackets.pcap -i eth0 dst 10.181.140.216 and port 22
——————————————————————————–
Capture TCP communication packets between two hosts
——————————————————————————–
$tcpdump -w comm.pcap -i eth0 dst 16.181.170.246 and port 22
——————————————————————————–
15. tcpdump Filter Packets – Capture all the packets other than arp and rarp
——————————————————————————–
$ tcpdump -i eth0 not arp and not rarp
20:33:15.479278 IP resolver.lell.net.domain > valh4.lell.net.64639: 26929 1/0/0 (73)
20:33:15.479890 IP valh4.lell.net.16053 > resolver.lell.net.domain: 56556+ PTR? 255.107.154.15.in-addr.arpa. (45)
20:33:15.480197 IP valh4.lell.net.ssh > zz.domain.innetbcp.net.63897: P 540:1504(964) ack 1 win 96
20:33:15.487118 IP zz.domain.innetbcp.net.63897 > valh4.lell.net.ssh: . ack 540 win 16486
20:33:15.668599 IP 10.0.0.0 > all-systems.mcast.net: igmp query v3 [max resp time 1s]
——————————————————————————–
기타예제
——————————————————————————–
// 라우팅되는 패킷도 검사할수 있다.
sudo tcpdump -n -i wlan0 dst 172.20.10.1
################################################################################
tar 파일에 파일 추가 하는 방법
################################################################################
tar cvf vim.tar.gz .vim
tar –append –file vim.tar .vimrc
################################################################################
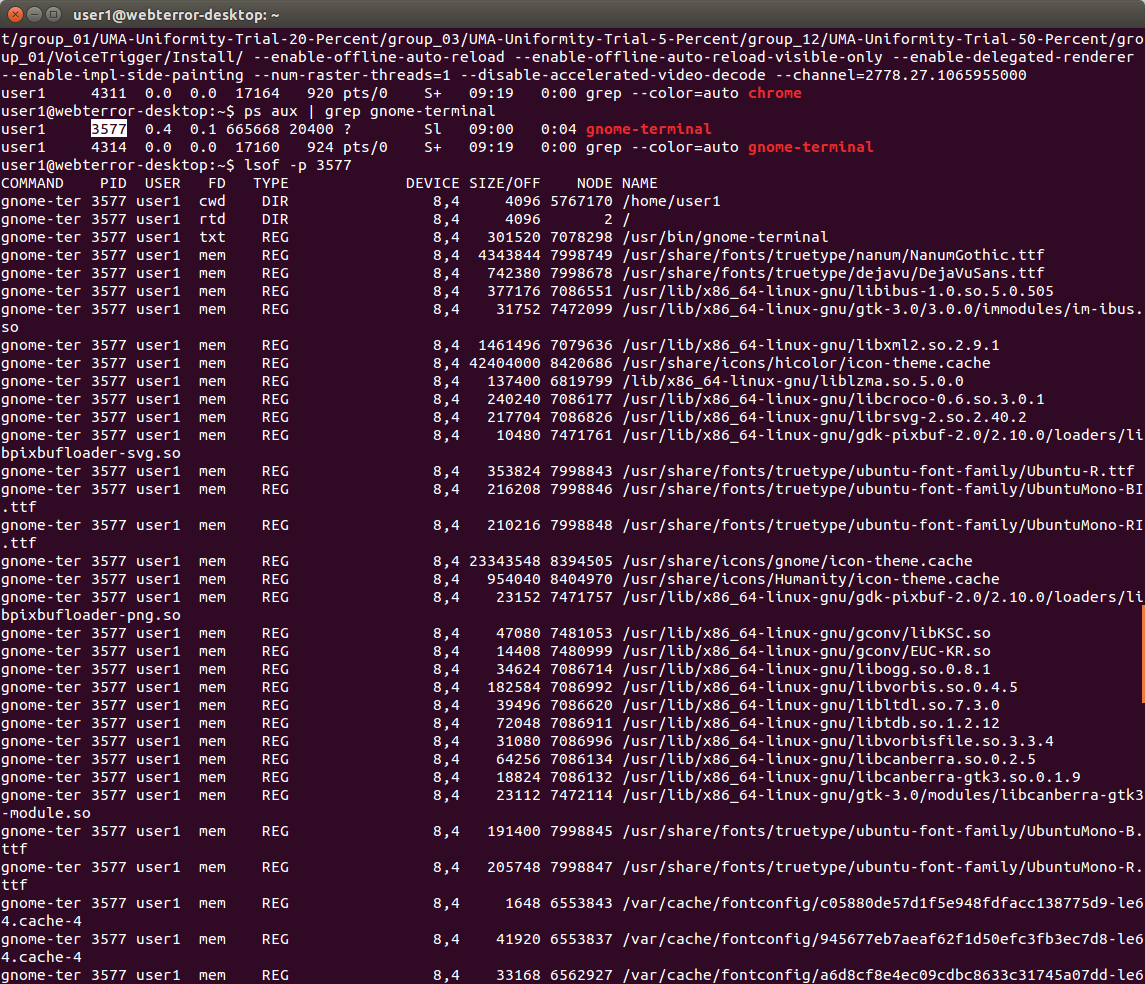
프로세스 자원 살펴보기
################################################################################
ps aux | grep synergys
프로세스 번호를 알아낸뒤
lsof -p 2416 다음처럼 자원 목록을 살펴본다.
################################################################################
7z 압축리스트 풀기
################################################################################
webterror@mlinkkorea-webterror:~/Downloads$ 7z e azdesign_ME3_jellybean_custompack.7z.001
################################################################################
tar 와일드카드 사용
################################################################################
@@ xml 파일들만 찾아서 tar 파일로 만드는 방법
find *.xml | xargs tar cvf ANDROID__2014_03_21_XML.tar;
################################################################################
IP 충돌 확인
################################################################################
sudo arping -I eth0 130.68.49.35
sudo arp-scan -I eth0 -l
sudo arp-scan -I eth0 -l | sort
################################################################################
SUDOER 추가하기
################################################################################
sudo usermod -a -G sudo
################################################################################
링크디렉토리 최종 목적파일 알아내기
################################################################################
readlink -f /usr/bin/java
################################################################################
스레드 카운트 세기
################################################################################
user1@webterror:~$ ps -o pid,comm,user,thcount 7198
PID COMMAND USER THCNT
7198 chrome user1 8
################################################################################
UUID 생성하기
################################################################################
$ uuidgen -r # random based UUID/GUID
$ uuidgen -t # time based UUID/GUID